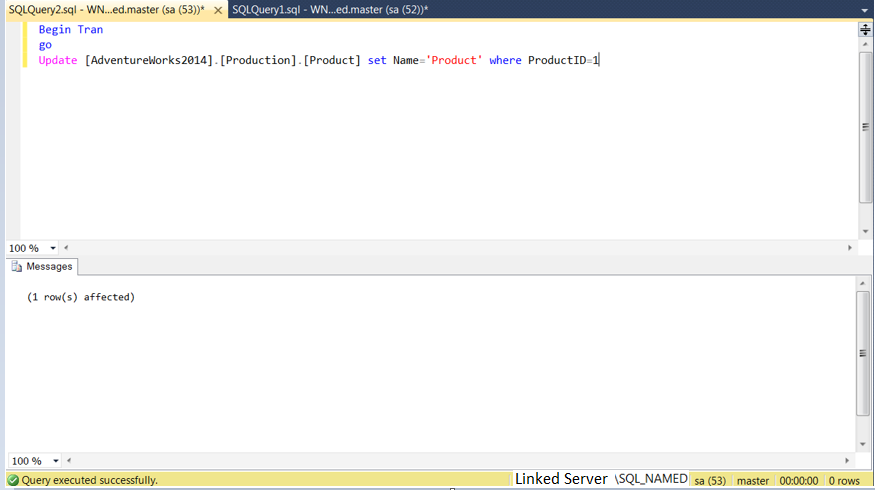
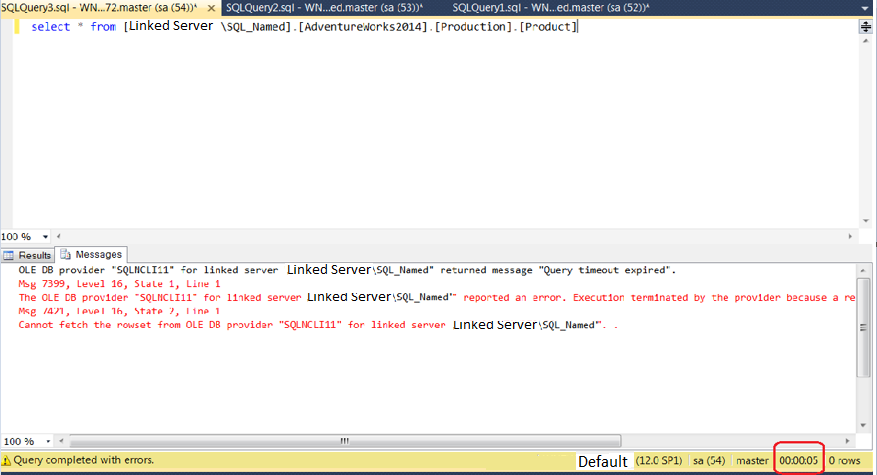
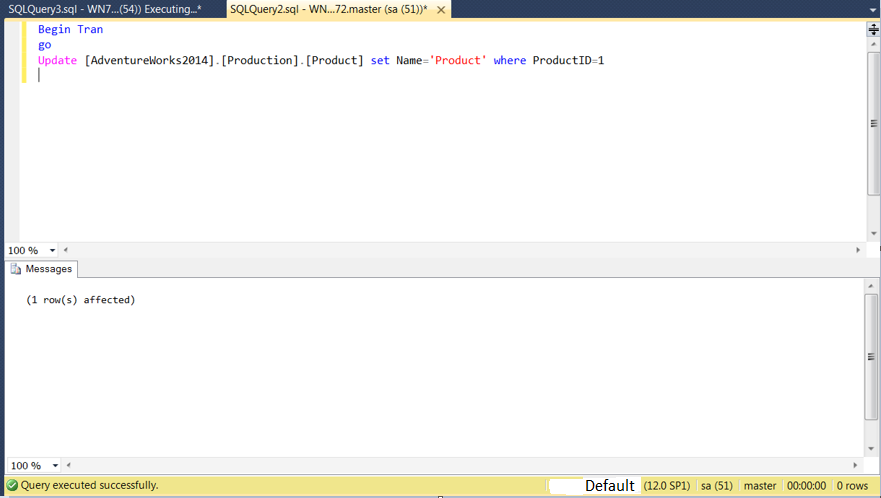
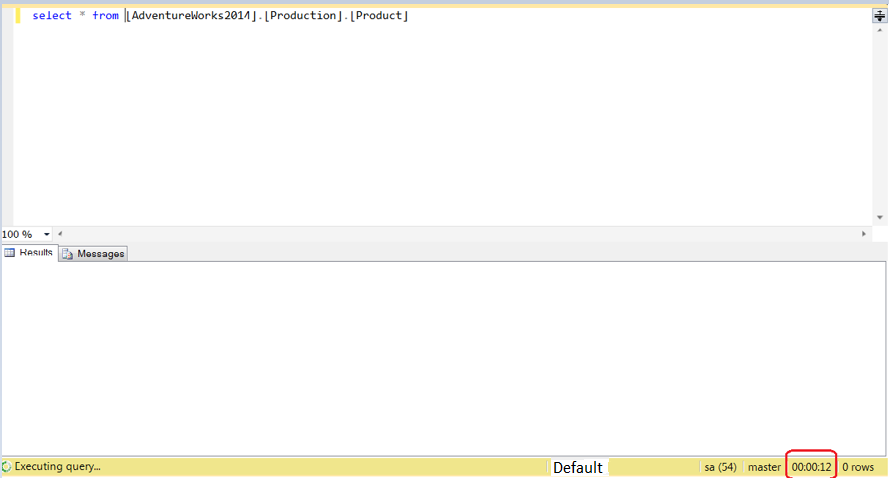
We all know that that Microsoft SQL Server uses many different ports to access various components of the product. In this article we are going to discuss about TCP and UDP ports.
To begin with, Ports are nothing but communication channel to manage system messaging among several different applications.
TCP and UDP Ports:
TCP stands for Transmission Control Protocol. The computers (Servers) connected to the Internet use TCP/IP to communicate with each other. In other words TCP/IP is a connection-based protocol. I.e. The sender sends numbered packets across the wire and the receiver checks and makes sure it got the correct packet.
Hence TCP/IP protocol is more safe and reliable. However it puts a higher load on the computer as it has to monitor the connection and the data going across it.
UDP stands for User Datagram Protocol. UDP protocol prefers speed over reliability. That is to say UDP does not connect directly to the receiving computer like TCP does, but rather sends the data out and relies on the devices in between the sending computer and the receiving computer to get the data where it is supposed to go properly.
You can think of the postal dept. as a practical example. The sender place mail in the mailbox and hope the Postal Service will deliver it to the proper destination address. Most of the time it works but sometimes it fails to deliver.
What are the SQL Server TCP and UDP ports?
The default instance of the SQL Server Database Engine listens on TCP port 1433. The named instances uses dynamic port. When you are connecting to a named instance through a firewall, configure the Database Engine to listen on a specific port and open that particular port in firewall.
1433 port is also the official Internet Assigned Number Authority (IANA) socket number for SQL Server.
The SQL Server Browser service listens on UDP port 1434 for incoming connections for named instance. The service then responds to the client with the TCP port number for the requested named instance.
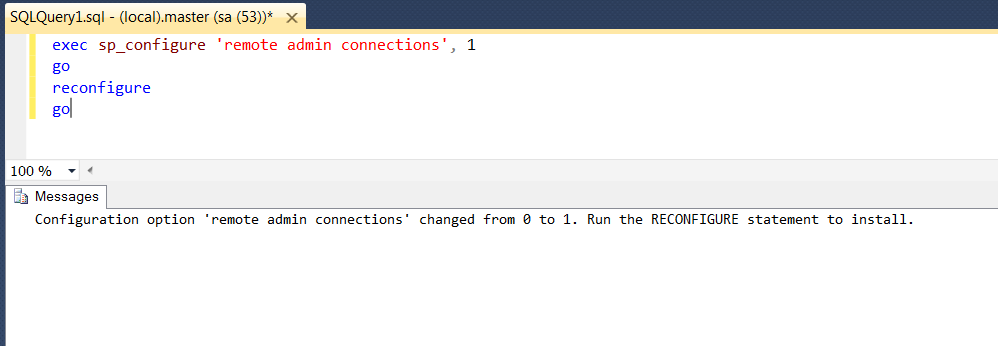
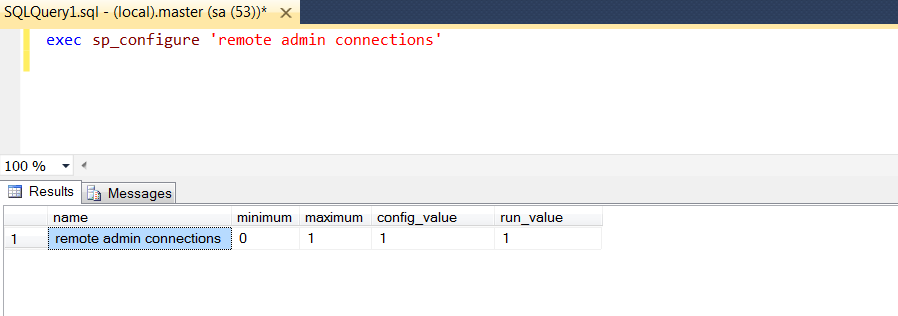
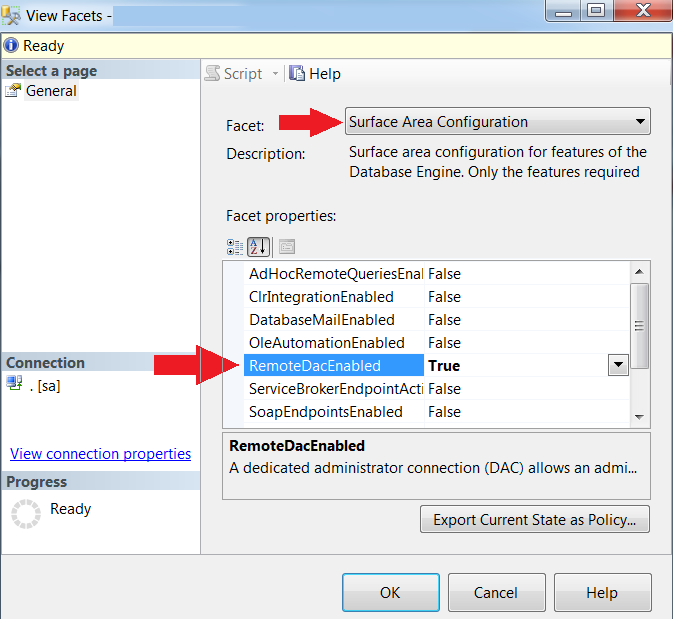
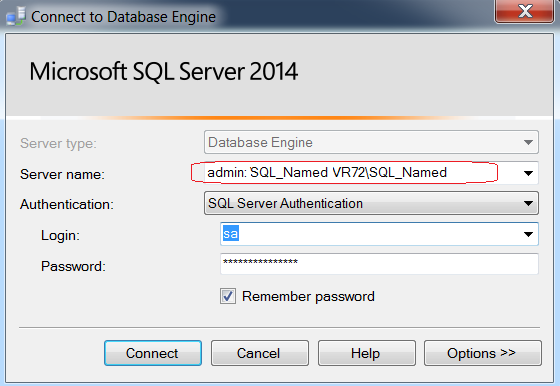
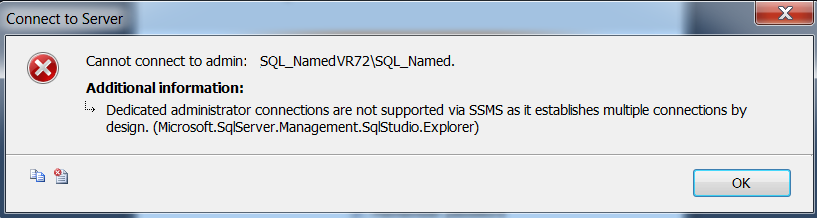
Point often overlooked is TCP port 1434 (Yes, you read that correct) is the default SQL port for the Dedicated Admin Connection.
TCP port 2383 is the default port for SQL Server Analysis Services.
Refer the Microsoft link All SQL Server Ports for more details.
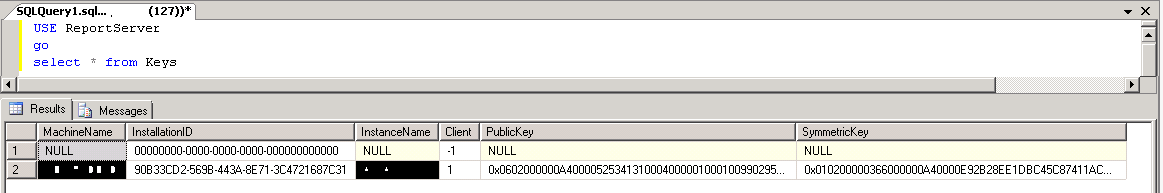 As you can see no information about location of keys or at least last backup information.
As you can see no information about location of keys or at least last backup information.
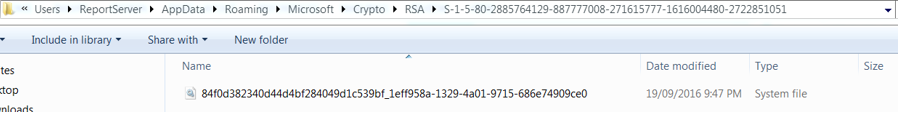
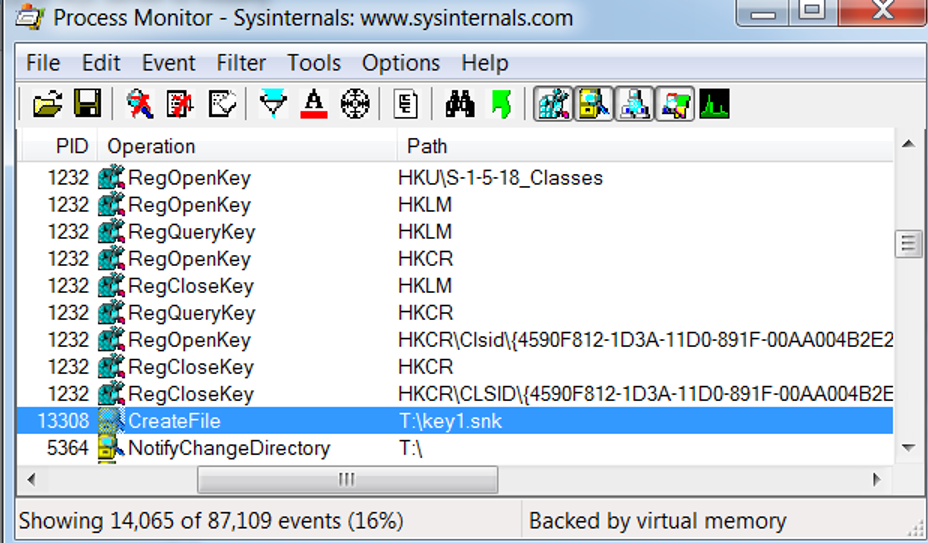 I could see that the path showing the key backup as shown in the above screen shot.
I could see that the path showing the key backup as shown in the above screen shot. This “Cannot find string” message shattered my hope 🙁
This “Cannot find string” message shattered my hope 🙁